Biometric authentication is becoming ubiquitous on mobile devices, where users routinely unlock their smartphone using a fingerprint or the face.
This is usually perceived as very secure, indeed biometric authentication complies with the principle of using multiple independent factors for user authentication, in this case something that the user is or does, as opposed to passwords (something that the user knows) or security tokens (something that the user has).
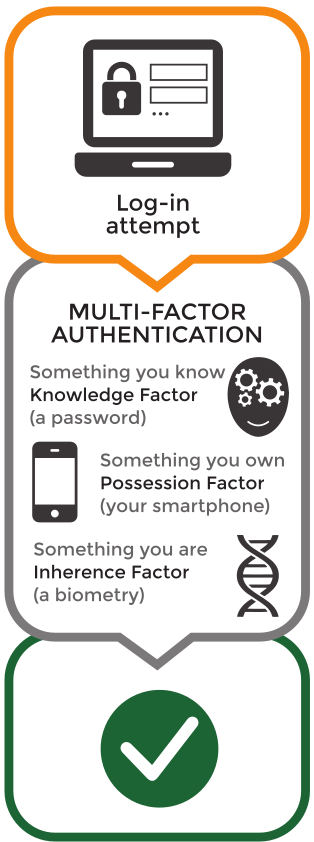
Nevertheless, even biometric authentication has vulnerabilities.
Differently from passwords and security tokens, a biometric feature cannot be replaced. If passwords are usually sent to a remote server to perform user authentication, sending fingerprint or face data to a remote server would expose the user to much higher risks, since the disclosure of biometric data would be irreversible.
The currently accepted solution is that biometric data never leaves the mobile device. Biometric authentication is performed entirely within a secure area of the device, a Trusted Execution Environment for Android or a Secure Enclave for iOS. Data acquired by a biometric sensor are directly sent to this secure area using a protected channel. Biometric templates are stored in the secure area. The comparison of live data with stored templates is entirely performed in the secure area. So far so good.
However, the above scheme delegates biometric authentication to the mobile device. The remote server is not directly comparing a live fingerprint with a stored fingerprint. The remote server is trusting the mobile device with this task. Hence, before trusting the answer provided by the mobile device, the remote server must in the first place ensure that on the other side of the communication channel there is the right device.
In the mobile ecosystem, biometric authentication requires device authentication.
What if device authentication is broken? A fake device could pretend that biometric authentication has been performed correctly even without the correct biometric data. In short, breaking device authentication completely bypasses biometric authentication.
Current implementations exploit secret keys stored in the secure area to identify the device. However, this is not always the best possible solution. Ideally, device identification should depend on something unique and unclonable: only a particular device has it, it cannot be copied and transferred on another device. Hardware Physical Unclonable Functions are an optimal solution in this sense.
Unfortunately, hardware PUFs can be expensive and require a complete hardware re-design.
Luckily, every smartphone already has the equivalent of a hardware PUF: the camera sensor. Camera sensors leave in the acquired pictures invisible traces, due to slight fluctuations in the sensitivity of the sensor pixels. Those traces are unique and unclonable. Only that sensor leaves them. It is not possible to build a second sensor with the same traces.
ToothPic SDK is able to harness the power of those traces. It can link a secret key to the camera sensor. Only a device with the same camera sensor will be able to reproduce the same secret key. So, this is the strongest possible device identification.
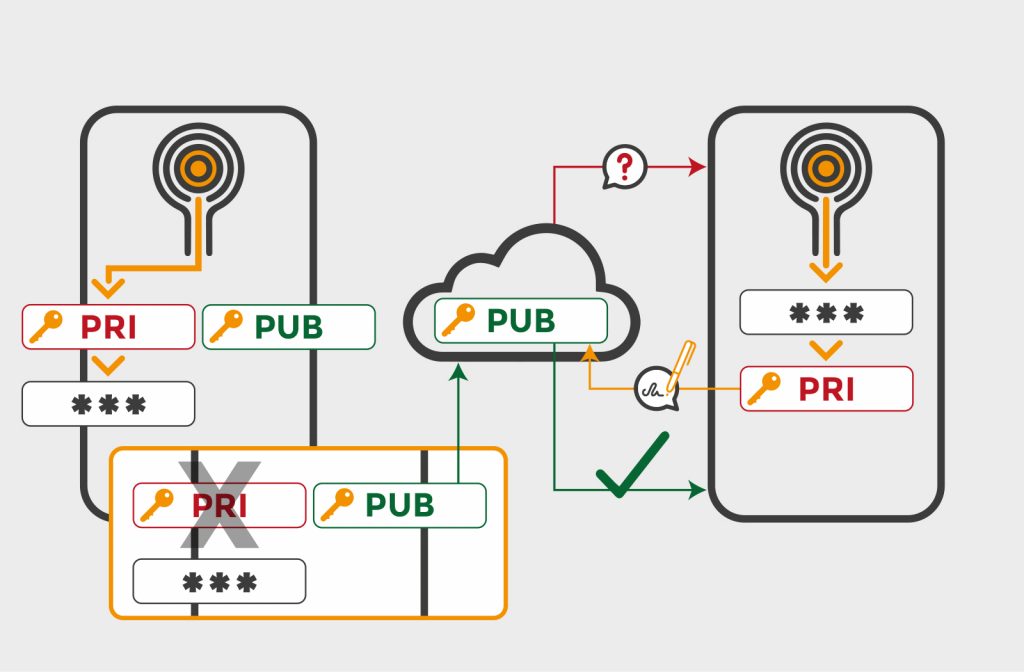
ToothPic does not provide biometric authentication; but in the mobile ecosystem, a solution like Toothpic’s one can greatly improve the security of biometric authentication.


