
Camera fingerprints
Your smartphone is unique because its camera is
Every picture taken by a smartphone contains an invisible trace, which is called PRNU (Photo-Response Non-Uniformity). This trace is unique – making every camera sensor different from each other – just like a fingerprint. This fingerprint is also completely random, because it is intrinsic to manufacturing processes of sensors. Being random means that the producers of sensors and smartphones cannot manipulate it, or clone it in a different sensor, making this characteristic a Physical Unclonable Function (PUF) by design.
ToothPic exploits the camera sensor fingerprint to derive a secret that ties keys to the sensor hardware
Asymmetric Cryptography
Your secret is only on your smartphone
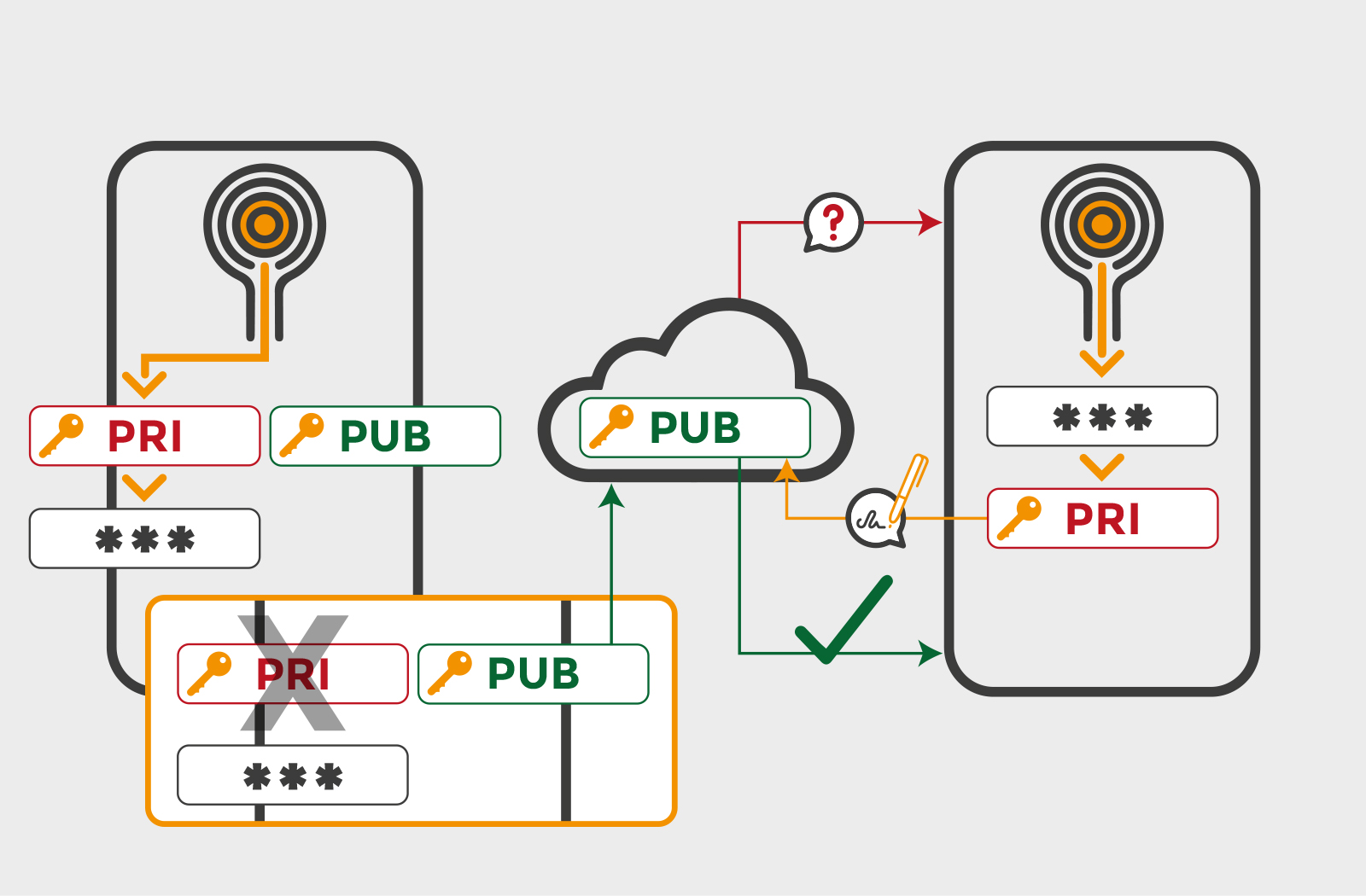
With asymmetric cryptography a user has a private key that should be kept safe and a corresponding public key shared with everyone. Operations performed with one of the keys can only be verified using the corresponding other key. For user authentication a simple protocol can be established: the server sends a challenge message to the user, the user signs the message using the private key, the server verifies the signature with the user’s public key. Since there is no shared secret between the server and users, there is no single point of failure at the server side. The only requirement is to protect each users’ private key. Due to its enhanced security, this is the solution chosen by most recent authentication protocols like FIDO.
ToothPic keeps private keys safer than competing technologies, since they are never stored on the device but tied to its hardware.
Secure Computation
Do not expose your secret to malware
As users of Internet-based services, we know we are constantly subject to attacks aimed at stealing our secret keys. Also the information stored on your smartphone can be subject to attacks. Indeed, malicious software may be installed on it, and it may read and use sensitive information. For this reason, the best smartphone-based cryptographic systems do not store data and perform calculations like any other app does — they use secure computation environments that guarantee application integrity and data confidentiality. This can be done using e.g. the trusted execution environment or whitebox cryptography techniques.
ToothPic provides maximum protection of the secret on your smartphone, as it performs computations in a secure environment – and unlocks it upon sensor hardware verification.

